Probably, the most common question I get from my non-technical friends and family members are: “Should I get a VPN?”. With the implied addition, “in order to be more secure”. Usually, my answer to this tend to be No followed by, well, it depends. And since the “it depends”-answer is nonsense without also explaining what those dependencies are, I need to go into an explanation about how VPNs work, what problems they solve and under what circumstances they make sense and under what circumstances they do not. Given the many times I have given the same answer, or variations of this answer, I thought that it could be nice to write it down to give people a resource that they can share to whoever also has the question.
Before we dig further into the answer to this question, I would like to reflect a bit on why I keep getting this question. There could of course be many reasons for this, but I think that one reason, or at least part of the reason, is a confusion about what a VPN does. And I think that a reason for that is due to the VPN companies marketing [1], where they reference cyber security threats that many people are indeed facing, such as online tracking, phishing, malware, etc. and may be more or less aware of. They then push their VPN product as the silver bullet solution to all these problems. And while it is true that many providers offer ad-on services to their VPN which may or may not be good at protecting against these threats, the distinction is not made clear enough for people to understand where the VPN ends, and some other product starts. This is likely done due to marketing reasons, it is easier for the customers to understand the problem solved by a product this way. I would, however, say that this is actively harmful as it will make less technical users draw a mental equal sign between VPN and privacy and think that whatever VPN service they pick up will automatically provide all the same protections when they in fact do not.
Alright, enough speculations and let us proceed with some more facts.
How does a VPN work?
Before we can talk about how VPNs work, we need a basic understanding of how network traffic in general works. But before going ahead with that, I would like to make a disclaimer that networking is quite complicated and since this post is directed towards everyone who is not a networking nerd already, I have made a lot of simplifications in favour of pedagogy.
Everything that is connected to the internet has an IP address. Such an address might look like: 192.168.2.1 (this address could for example be your router). This address is a global identifier of an internet connected device. This means that all your devices such as your phone, computer, smart TV etc. has one. It also means that every server on the internet has one, which in turn means that every website you are visiting has an IP address, even though you typically visit it using its domain name (for example linuslagerhjelm.se). As you may know, the internet is pretty big, both in strictly geographical terms (it is world-wide after all), but also in terms of connected devices. These two things make it terribly inconvenient to connect your devices (e.g., your cell phone) with a physical wire to each server hosting each website you would want to visit, as that would be plenty of cables going out of your smartphone all the way to the server, which might be located across the Atlantic Ocean. Instead, we use the IP address of the server we want to connect to and then we only communicate with the device that is nearest to us. On our home networks that would typically be our router, which then forwards our data to another router and so on, until it eventually reaches its destination, the device with the destination IP. In order to keep track of all of this when the data moves around on the internet, the data is arranged into a little packet, much like a postal packet, but in this case, it is an IP packet. A conceptual image of that can be seen bellow:
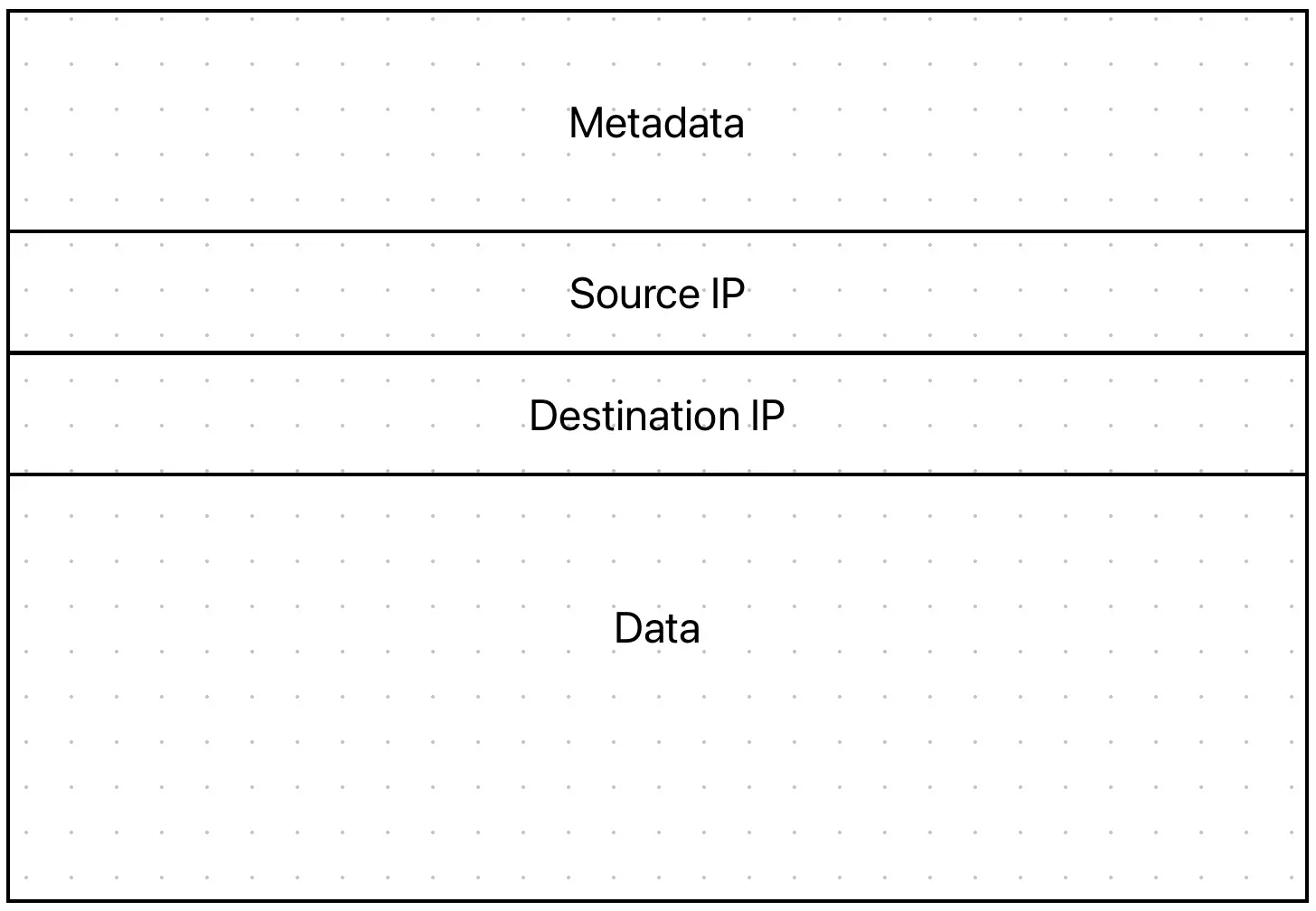
So, an IP packet contains our data, but it also contains information about who should be receiving this packet (the destination IP), who sent it (sender IP) and there is also some metadata about the packet. This metadata includes things like what protocol version etc. that is needed for intermediate devices to know how to handle the packet, however they are not that important for us in this discussion. Inside the data field of the packet is where the data that you as a user care about is being stored. It could for example be an image you want to download from a website. So when the website sends you the data, it creates such a packet and enters your device’s IP address as the destination IP and its own IP as source address and sends it to its nearest device, who in turn looks at the destination address and forwards it to some other device close by that is closer to the destination, and so on until it reaches your device. This setup is very robust and reliable; however, this does create security problems. Since you are not sending your packets directly to the recipient, but also to a long chain of intermediaries, the communication between the sender and the receiver is not private. Everyone in the chain will be able to see who sends the image to who and will also be able to see the image. The second problem can be solved by using encryption, which is the case when you are using HTTPS (such as when navigating to a website with a green padlock). It is consequently not a problem that we need a VPN to solve. What a VPN could solve for us, however, is the problem that everyone is able to see who is talking to who. And an illustration of how that works is found below.
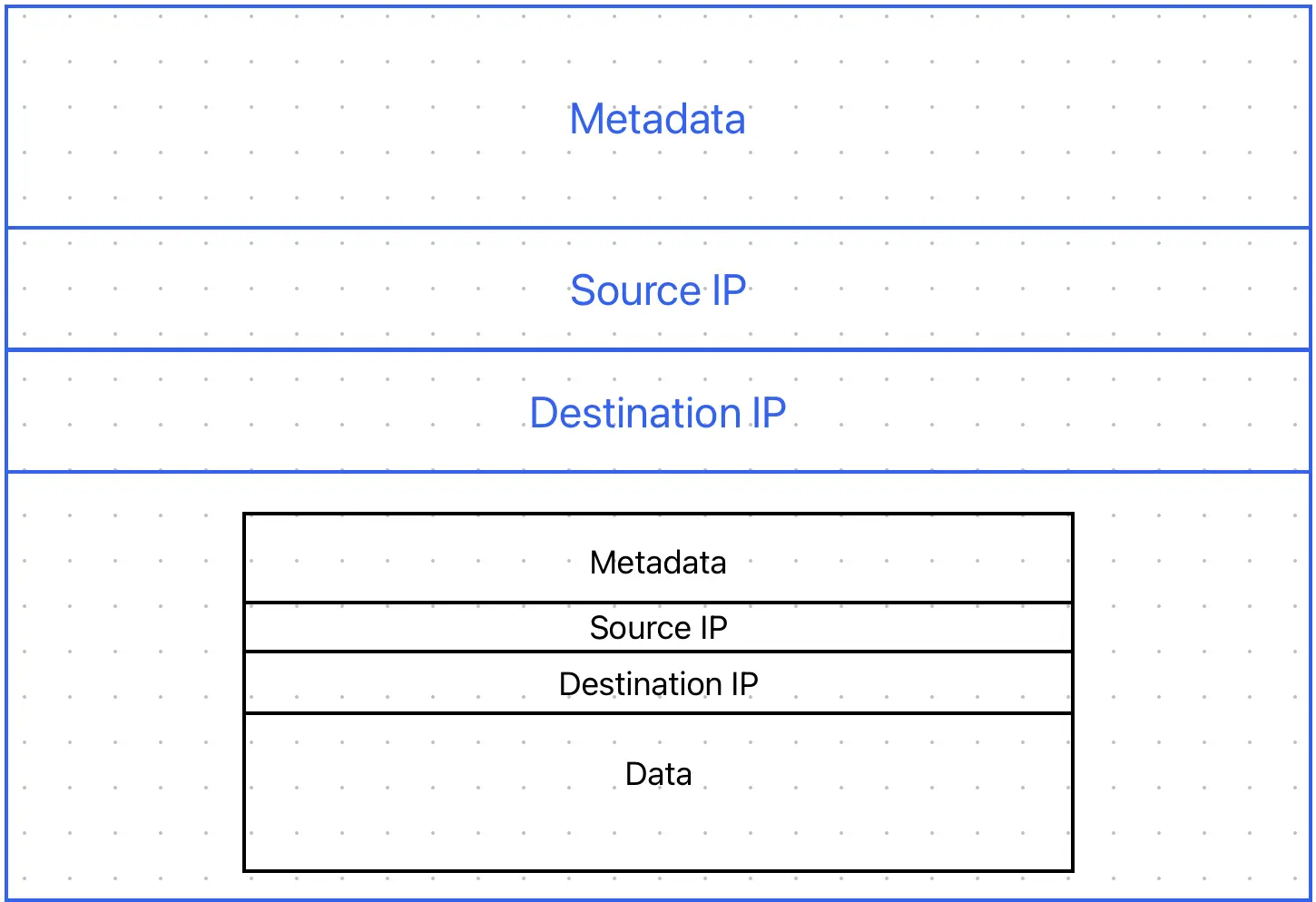
When a user is using a VPN, the VPN client that is installed on the user’s device will take all packages that the users is sending, and wrap them in another packet which, instead of the original destination address, has the IP address of the VPN server in its destination IP. It will also rewrite the source IP field of the inner packet to the same value, the address of the VPN server. This, rather confusing description might be easier to understand if you look at the below illustration which depicts this.
Using a VPN like this will allow us to hide our IP address from the one we are communicating with, as to them, it will look like all the traffic is coming from the VPN server and they will not know that the VPN server forwards the packets to us. This flow can be seen in the bellow image.
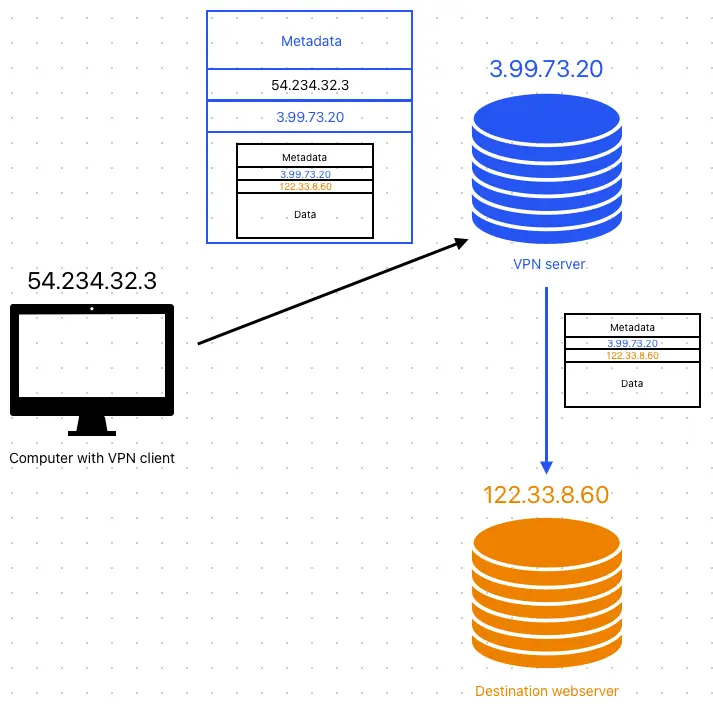
Typically, a VPN will also encrypt the data in the body, rendering it unreadable to anyone that is not the VPN client or the VPN server however, it is not necessarily the case.
Are there any downsides of using a VPN?
Aside from any perceived benefit of using a VPN, they also introduce plenty of risks and other downsides. Here is a list of the most common ones.
Shady actors
This is the main risk with using VPNs and it is actually a catch all label for multiple separate risks that all stem from the same fact: that you are using a un-serious VPN provider. As explained in the previous section, a VPN operator will act as sort of a middleman between you and whoever you are talking to, which means that you will entrust them with quite a lot of power over your connection. Since all traffic is routed through the VPN service, they will be able to read all your data, even if no one else can. There are plenty of known cases [2] of where VPNs, especially free ones, sell your data to third parties or it might use your data to show you targeted ads, which it can do because it will under some circumstances be able to change the content that is being sent to your device. Even if you pick a paid alternative whose business model does not depend on selling your data, the VPN service could still be logging your activity. This could be done for technical rather than nefarious reasons, however if the data is there, it could be stolen. Either if the VPN service provider suffers a data breach or is subject to a warrant from the government. Bad actors may also steal passwords and banking information when you are filling out login/checkout forms online.
DNS leak
The short version of a DNS leak is that your (approximate) physical location might be leaked if you have a misconfiguration in your VPN setup. Which would greatly undermine the purpose of having it.
The technical reason for this is due to a protocol called DNS. Us humans do not really like to remember IP addresses as we are not very good at remembering numbers. Instead we prefer to navigate to websites using a human readable address, such as www.linuslagerhjelm.se. However, since computers only communicate with each other using IP addresses, there is a need for the device to translate the website address into an IP address. This is the purpose of DNS and basically how it works is that if you enter www.linuslagerhjelm.se into your browser, your device will start by asking a name server, i.e., a server on the internet whos only purpose is to know the IP addresses of URLs, on what IP address this website can be found. These name servers are organized in a hierarchical manner, so your computer will start by asking your ISP of the location of www.linuslagerhjelm.se and if they do not know, they will forward the question for you and eventually it will end up with the name server of the .se domain. This server knows where to find linuslagerhjelm.se as it is a direct subdomain of .se. However, it does not know where to find the subdomain www. of that URL, so it must in turn forward the request to the authority that knows this. In this step, the afore mentioned authority might be able to see information about your IP, such as what ISP you are using and approximate geographical location.
It is very common that this DNS request goes directly to the name server instead of going through the VPN tunnel, and thus, it will leak information about you that you probably wanted to hide.
Reducing connection speed
Using a VPN will add more complexity to your network. Instead of letting your traffic go straight to where it is going, you are forcing it through a second server, which will add network latency and depending on the capacity of the VPN server, your performance could be even further decreased.
Blacklisting
Some internet services will blacklist the IP addresses of certain VPN servers. This could be done for any number of reasons, for example Netflix blocking VPN traffic to try to enforce geo restrictions, or it could be because another customer of the VPN has been abusing an online service in one way or another. In the case of IP blacklisting, you might end up in a situation where certain online services are unavailable to you, even if they would be available, had you not used a VPN.
Conclusions
VPNs has the potential of making the user more secure. However, that potential can only be realised if the VPN service provider is serious, both in terms of not actively wanting to fraud or abuse you but also in terms of skills, as it is very easy for even a well intended actor to get configuration wrong. This means that it is crucial to perform a thorough due diligence before choosing a provider. And by that, I mean extremely serious, it is not enough with a short googling session because it is very likely that it will result in you ending up paying for the privilege of having your data stolen and sold to some third party.
All the above, together with the fact that a VPN will also reduce, sometimes even significantly, your internet speed makes it in my opinion extremely unlikely that a VPN is a good idea from a security perspective. Although there are some valid scenarios for a VPN, people in those scenarios are typically qualified enough to know and weight the risk of using a VPN vs not using it.
Lastly, I also want to mention that if you happen to be one of those users that do not want to use a VPN primarily for security but for e.g., circumvent geo blocking on streamed content, a VPN might help with that, but it will also introduce all of the above risks, so it might be worth thinking twice about using it.
